Welcome to Pradeep’s Cybersecurity Hub!
I’m a cybersecurity professional with 2+ years of dedicated experience in security operations, threat detection, and incident response. I hold a Master’s in Cybersecurity from California State University, Dominguez Hills, where I focused on SOC operations, SIEM analysis, MITRE ATT&CK, and threat hunting.
I’ve responded to real-world security incidents in a 24x7 environment, fine-tuned SIEM rules in Splunk and ELK Stack, and investigated network traffic using IDS/IPS tools. My hands-on lab projects span firewall log analysis, packet capturing with Wireshark, protocol simulation with Scapy, and building adaptive detection systems with Docker and Terraform.
I’m passionate about continuous learning and sharing knowledge — through my community hub,
L-Earn Cyber, I’ve authored 20+ technical articles and hands-on guides covering SIEM, EDR, and best practices for defending modern environments.
👉 Let’s connect, collaborate, and strengthen our defense strategies together.
Hello,
Pradeep here !
scroll down...



CERTIFICATIONS


BLOGS
L-earn cyber is a dedicated platform where I share my blogs and write-ups. it is started with a strong initiative to share the knowledge in the domain of cyber-security. The write-ups in the page is a reflection of my cyber journey.
click on the logo to see my page.....
Scroll down.....

PROJECTS


Security Log Investigation Using Splunk
COURSE WORK
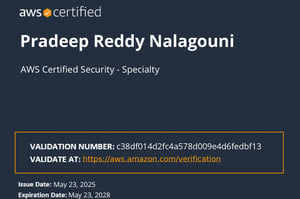
AWS SECURITY
Secure File Processing Pipeline on AWS
Course Project | AWS Cloud Security & Automation
Designed and deployed a secure, event-driven file processing system using S3, Lambda, SNS, and EC2, allowing automated extraction of metadata as soon as files were uploaded.
Applied KMS encryption on S3 buckets to protect data at rest and configured IAM roles to tightly control permissions across services.
Set up S3 event notifications to trigger Lambda functions for real-time processing and used SNS to notify subscribers instantly when new files were added.
Ensured security through least privilege access, cross-service policy validation, and adherence to AWS best practices.
This hands-on project helped me deepen my understanding of server less design, secure storage, and cloud automation in a production-like environment.
VPC Security Lab Implementation
Course Project | AWS Networking & Security
Built a custom VPC architecture with public and private subnets, route tables, NAT Gateway, and Bastion Host to simulate a secure cloud environment.
Configured Security Groups, Network ACLs, and IAM policies to enforce strict access control across EC2 and S3.
Validated configurations by performing real-time SSH/HTTP access testing, port scanning, and traffic analysisusing VPC Flow Logs and CloudWatch.
Introduced automation via AWS CLI and infrastructure-as-code scripts, making deployments consistent and reproducible.
Gained practical experience in network segmentation, secure connectivity, and compliance-ready architecture, aligned with cloud security standards like PCI DSS.
Scalable Architecture with Load Balancing & Auto Scaling
Course Project | AWS Infrastructure & Performance
Created a high-availability web application architecture using EC2 instances, Application Load Balancer (ALB), and Auto Scaling Groups.
Developed scaling policies based on CloudWatch metrics to automatically adjust instance count, maintaining performance during variable traffic.
Configured ALB listeners and target groups to route traffic efficiently, and tested the system’s response under simulated load conditions.
Automated environment setup with EC2 User Data scripts, reducing manual configuration time and improving consistency across instances.
This project reinforced my ability to build resilient, cost-optimized cloud solutions using AWS-native tools and real-time monitoring strategies.
Conducted a series of real-world log analysis assignments using Splunk to detect suspicious activity across firewall logs, Windows event logs, and web server logs. Designed custom queries and dashboards to uncover potential threats, visualize traffic behavior, and simulate SOC investigations.
Investigated firewall logs to identify denied traffic, port scanning activity, and malicious IPs.
Analyzed Apache logs to trace unauthorized access attempts and unusual browsing patterns.
Parsed Windows Security Event Logs to detect failed logins, privilege escalation, and lateral movement indicators.
Created a simulated SOC report with event classification, risk assessment, and recommendations.
Built an automated incident response workflow using SOAR concepts to improve alert triage efficiency.
Developed SPL queries to extract relevant insights, supporting both real-time monitoring and historical threat correlation.
This project strengthened my operational knowledge of how logs are used in security monitoring and incident response environments, and how to extract meaningful context from raw machine data.
https://github.com/pradeepreddy-code/network-packet-capturing-.git
Network Packet Capturing and Protocol Analysis


Designed and executed a series of hands-on assignments focused on deep packet inspection, protocol behavior, and network-layer attack simulation. Used tools like Scapy, Wireshark, and Python sockets to create, capture, and analyze traffic in controlled environments—mirroring real-world adversarial scenarios.
Created and transmitted custom TCP/UDP packets to understand header structure, data flow, and behavior under abnormal conditions.
Captured live traffic using Wireshark and Scapy to analyze port scans, malformed packets, and session persistence techniques.
Simulated attacks such as Smurf, Teardrop, and WiFi jamming, and documented both offensive behavior and defense strategies.
Performed wireless network analysis, including WPA2 handshake capture and network reconnaissance using beacon/probe requests.
Developed Python scripts to automate traffic scanning, socket communication, and protocol testing.
Mapped techniques to MITRE ATT&CK tactics such as network sniffing (T1040), service scanning (T1046), and DoS (T1498).
This project enhanced my ability to detect threats at the network level, understand how protocols can be exploited, and build stronger defensive controls based on observed traffic behavior. It reflects the foundational network knowledge expected of Security Engineers, SOC Analysts, and DevSecOps professionals.
https://github.com/pradeepreddy-code/splunk-log-investigation.git
File Firewall — End-to-End Secure File Access & Automation


Built a complete secure file protection system that automatically safeguards sensitive files with multi-factor authentication (MFA), a self-evacuation mechanism, and admin recovery. The system is fully containerized with Docker, deployed automatically using Terraform, and continuously monitored with Falco for runtime threats.
File Firewall Project Highlights:
Protects sensitive files with password + MFA (Google Authenticator)
Auto-evacuates files to hidden vault after 3 failed login attempts
Admin recovery mode to securely restore files with extra authentication
Fully Dockerized for portable deployment
Automated with Terraform (Infrastructure as Code)
Monitored by Falco for real-time runtime security alerts
This project demonstrates my ability to integrate secure file access controls, automate infrastructure using Terraform, containerize applications with Docker, and monitor runtime threats with Falco — showcasing strong DevSecOps skills and practical cybersecurity defense implementation.
https://github.com/pradeepreddy-code/file-firewall-automation-docker-terraform-falco.git

TO CONNECT WITH ME .......


Feel free to Reach out for collaborations or just a friendly hello.....